
Secure Dedicated Cloud
Cyber security is critical for all cloud services - consider it the heart beat of hosting your business. File and databases servers, email and web servers are an indispensable part of most business processes, and cyber attacks have direct negative effects on business reputation, data privicy, productivity, sales, employee and customer satisfaction. That's why we developed a secure dedicated cloud solution for you. Your dedicated cloud infrastructure is fully isolated from the others. All dedicated cloud infrastructures come with DDoS Protection, Firewall and IPS System. You have your own Cyber Security Operations Centre at your control panel. It is a secure clouod service leading the industry.
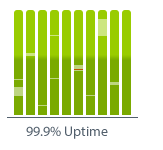
By trusting us with your business needs, we promise you a 99.9% uptime on any services we provide, outside of any standard maintenance we may provide.
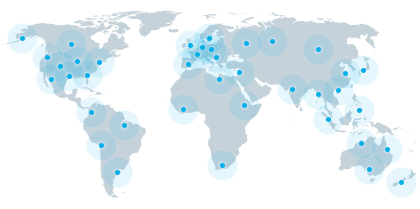
World Wide Data Delivery
Our services are powered by hundreds of servers and data centers located all over the world, so you can rest easy knowing that customers can access your website from anywhere. In addition, we provide monitoring tools to provide you with expert analytics - website traffic is an important step in improving your site's efficiency and popularity, as well as keeping track of where your visitors are coming from, what time of day they're visiting you, and how long they're staying. Our dedication to a global marketplace extends to data analysis and vulnerability management, as we offer user behaviour analysis and red teaming exercise.
Our dedication to customer support reaches across the globe as well. We are here to help you with your hosting in any way possible, and you can reach us via support centre.
Top Tier Security
Rest easy knowing that we provide 24/7 security monitoring and DDoS protection. You take protecting your customer's data seriously, and so do we. Our security team and safeguards are on the job all day, every day to provide the level of security needed in today's digital age.
A wide range of security tools are at your disposal, including SSL certificates, DDoS protection, firewall configuration, intrusion prevention system, security monitoring services, VPN access, and more.

